Easy Way to Read a Ket Value From Ini With Powershell
Administrators can perform all typical registry operations using either the old-practiced "Regedit" user interface or the reg.exe utility. Simply there is another option — Windows PowerShell. PowerShell provides a large set of tools for interacting with the Microsoft Windows registry, either on the local machine or remotely.
In this commodity, we'll bear witness how to get, edit, create and delete registry keys with PowerShell, perform a search, and use PowerShell to connect to the registry from a remote reckoner.
Getting Registry Key Values Locally with PowerShell
To get the values of all the registry keys on a local automobile, nosotros commencement have to find the path to the registry. Let's get a listing of all the local drives:
get-psdrive
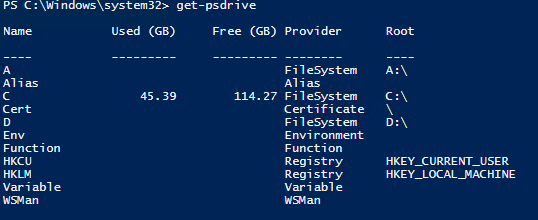
Equally you can meet, there are two entries for the registry: HKEY_CURRENT_USER (HKCU) and HKEY_LOCAL_MACHINE (HKLM). These are two logical groups of keys, or "hives," in the registry.
Therefore, nosotros can navigate to the local machine registry root key by running the following command:
cd HKLM:\
Alternatively, we can set our current working location to a particular path in the registry using the Fix-Location cmdlet:
set up-location -path HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\
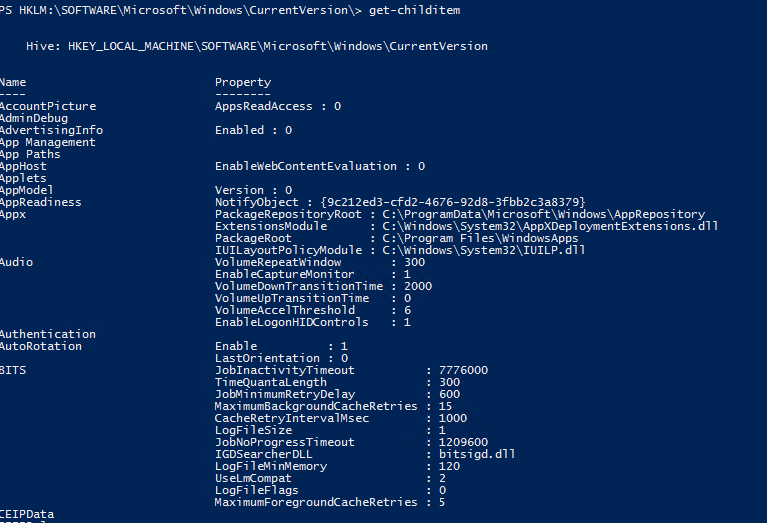
Then we can use the Get-ChildItem cmdlet to output all the registry keys in the current hive with their properties:
Go-childitem
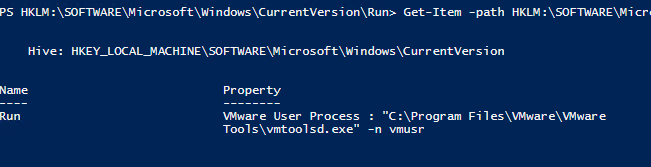
To become the parameters for a specific central (such equally the Run key), we would employ Become-Particular cmdlet, specifying the path:
Go-Item -path HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Getting Registry Key Values Remotely with PowerShell
PowerShell enables yous to connect to a computer'southward registry remotely and view it using WinRM. To do that, you demand to use the Invoke-Command cmdlet:
Invoke-Control –ComputerName dc1 –ScriptBlock { Get-ItemProperty -Path 'HKCU:\Software\System' -Name WorkingDirectory} Editing the Registry Remotely with PowerShell
To edit a registry remotely, we offset need to connect to it using Enter-PSSession cmdlet:
Enter-PSSession pdc -Credential Enterprise\T.Simpson
The arrangement will prompt you for the password for the user account y'all specified. After authentication, you lot will exist able to use PowerShell commands on the remote computer.
Searching in the Registry with PowerShell
To find particular keys in the registry, use a script like the following, which searches the registry for keys that contain "Netwrix" in their name:
become-childitem -path hkcu:\ -recurse -ErrorAction SilentlyContinue | Where-Object {$_.Name -like "*Netwrix*"} Editing the Registry with PowerShell
If we want to change one of the parameters for a registry fundamental, we need to use the Set-ItemProperty cmdlet. For example, we could utilise the post-obit command to set a new string value for the "VMware User Process" parameter of the "Run" key:
Fix-Itemproperty -path 'HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Run' -Proper noun 'VMware User Process' -value 'C:\Program Files\VMware\VMware Tools\vmtoolsd.exe'
Creating a Registry Primal with PowerShell
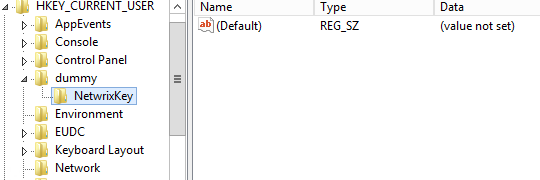
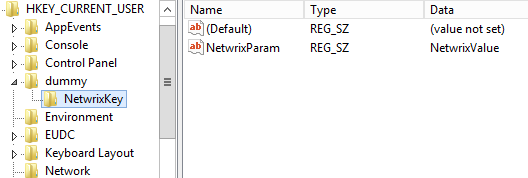
To add a key to the registry, we need to use the New-Item cmdlet. Allow'south create a new key named "NetwrixKey" in the KEY_CURRENT_USER hive:
New-Item –Path "HKCU:\dummy" –Name NetwrixKey
And now let's create a parameter called "NetwrixParam" for our new key and prepare its value to the string "NetwrixValue":
New-ItemProperty -Path "HKCU:\dummy\NetwrixKey" -Name "NetwrixParam" -Value "NetwrixValue" -PropertyType "Cord"
Let's accept a wait at information technology in the registry:
Deleting a Registry Key or Parameter with PowerShell
Now let's delete the "NetwrixKey" parameter we but created using the Remove-ItemProperty cmdlet:
Remove-ItemProperty -Path "HKCU:\dummy\NetwrixKey" -Name "NetwrixParam"
Then let'southward remove the key "NetwrixKey" itself:
Remove-Detail -Path "HKCU:\dummy\NetwrixKey" -Recurse
The –Recurse parameter authorizes PowerShell to delete all the subkeys without additional confirmation (of course, we didn't create any subkeys in this example).
If yous want to delete all subkeys inside the specified central without deleting the cardinal itself, you should add the "*" symbol at the end of the path:
Remove-Detail -Path "HKCU:\dummy\NetwrixKey\*" -Recurse
Renaming a Registry Key or Parameter with PowerShell
To rename a registry key, employ the Rename-Detail cmdlet:
Rename-Item -Path "HKCU:\dummy\NetwrixKey" NetwrixNewKey
To rename a parameter of a registry key, utilize the Rename –ItemProperty cmdlet:
Rename-ItemProperty -Path "HKCU:\dummy\NetwrixKey" -Name "NetwrixParam" -NewName "NetwrixNewParam"
Conclusion
Now y'all know the bones registry management capabilities of Microsoft Windows PowerShell. As you can run into, registry key direction is rather easy and fast — just remember, that fifty-fifty ane fiddling change can pb your operating system to the blueish screen of death.
Therefore, before you make whatever changes to the registry, you should be 100% sure of what you are changing, take current backups of your arrangement and data, and rails all the changes yous make. Netwrix Auditor for Windows Server can help; it tracks, reports on and alerts on changes to the Windows registry.

Source: https://blog.netwrix.com/2018/09/11/how-to-get-edit-create-and-delete-registry-keys-with-powershell/